Cybersecurity: The Next Trillion-Dollar Market?
February 22, 2019
Sid Trivedi
It seems like every couple of weeks, there’s a new frontpage story about our private information being hacked. Companies like Twitter, Equifax, Yahoo, LinkedIn, and most recently, Marriott and Quora, have all fallen victim to losses of over 100 million identities due to cyber-attacks. To put things into perspective, hackers stole information on as many as 500 million guests at Marriott. Two-thirds of those victims—330 million people, in other words, the size of the total US population—likely had their addresses, phone numbers, and passport details stolen. An attack of this scale results in technology, legal, and security expenses for years to come and will likely end up costing billions of dollars.
It should therefore come as no surprise that Gartner projects global cyber spending in 2019 to exceed $124B (~9% growth from 2018). And Accenture found, in a survey of 4,600 companies with over $1B in annual revenue, that two-thirds of CEOs and boards of directors have direct oversight of their cybersecurity leader. Investing in security has kept pace with this sector growth and according to data from Momentum Cyber, we ended 2018 with $6.2B of total capital raised by cybersecurity startups (a 15% increase from 2017), with 383 deals.
At Foundation Capital, since 2001, we have made 17 investments in cybersecurity, including MobileIron, ForgeRock, Carbon Black, Skycure and Venafi. In this blog post, we are sharing what themes will enable cybersecurity to become the next trillion-dollar market.
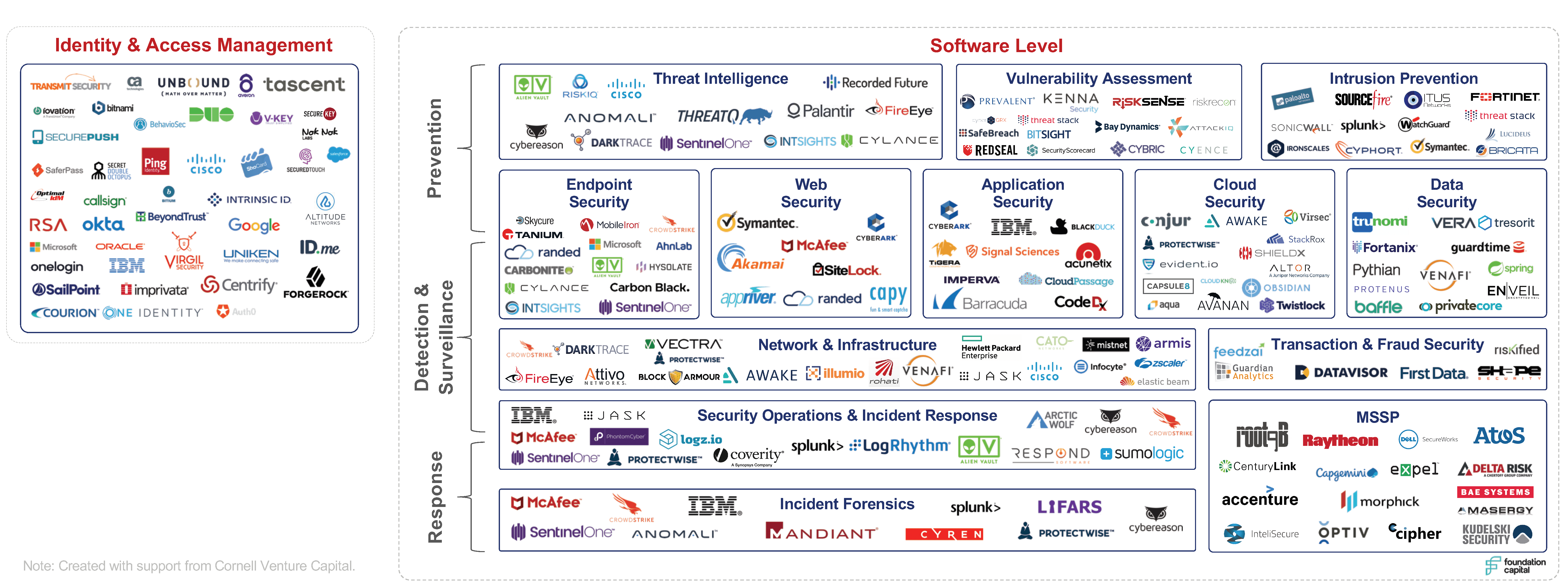
OUR VIEW OF THE CYBERSECURITY WORLD IN JANUARY 2017
In January 2017, we viewed the cybersecurity market as principally consisting of a software-based attack vector where there were three successive layers—prevention, detection, and response—and a tangential segment focused on identity and access management. This view is outlined in the following market map:
MARKET THEMES
Over the past two years, there are three key market themes that we have been tracking and that have helped us to develop our updated view of the cybersecurity landscape and our investment thesis in this field.
1. You can’t keep the bad guys out forever
Four years ago, the average security leader would allocate ~70% of their budget to pre-breach prevention technologies and ~30% of their budget to post-breach detection and response technologies. As the number and size of high-profile breaches has steadily increased, it has become clear from our discussions with security practitioners that they don’t believe their perimeter defenses are enough. In their minds, it’s not a question of if their perimeter has been breached, but whether they have enough visibility in their environment to detect and respond to these bad actors.
We are already seeing a change in budget allocation to adapt to this paradigm, but our belief is that as the security budget grows, the vast majority of this additional spending will go to post-breach detection and response technologies, and over time, the 70/30 split will flip.
2. The attack surface has increased exponentially
Over the past two years we have closely tracked the most notable cyber-attacks—WannaCry, NotPetya, and Spectre/Meltdown—and through our analysis of these attacks, we have realized that hackers have evolved their approaches on how to breach a company’s environment. This has led to the realization that we have been excluding two large parts of the attack vector: hardware (the IT, OT and IoT devices in an environment) and human (both employees and end customers).
Within the existing software-based attack vector, the fundamental shift that we are seeing is companies moving from an on-prem to a hybrid-cloud world. According to data from the Goldman Sachs CIO Survey released in December 2018, CIOs noted that 26% of their workloads are in the public cloud and project this number to increase to 38% by 2021. Security and data loss consistently come up as the two primary concerns for CIOs when asked what is holding them back from moving more of their workload (particularly production workload) to the public cloud.
3. It’s REALLY tough to find security talent
Because of the intense focus on IT security within a company, the demand for talent across the security organization is far outstripping supply. According to data from IDG and Symantec, the global demand for the cybersecurity workforce is expected to rise to 6M this year with a projected shortfall of 1.5M jobs. This means that 25% of available jobs are not being filled. According to data from recruiting firm Robert Half, employees across the security organization are seeing larger than average gains in pay with increases between 7-10% annually. In addition, through our own customer network, we are readily seeing over 20-30% increases in pay for security software engineers (average salaries of $230K), who are being poached by other companies.
FOUNDATION CAPITAL’S 2019 CYBERSECURITY LANDSCAPE
Based on the three market themes outlined above, we are releasing our updated map of the security landscape. In this new map, we break out our view of the cyber world into three broad buckets, which define three attack vectors that modern hackers use—software, hardware and human.
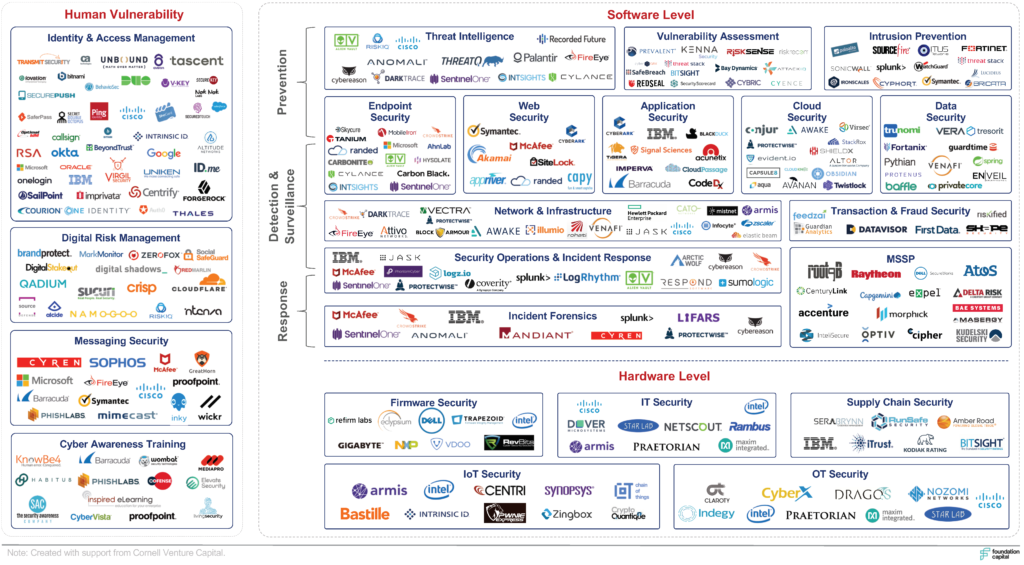
FOUNDATION CAPITAL’S 2019 CYBERSECURITY INVESTMENT THEMES
There are five themes that we plan to invest behind in the cybersecurity market:
- Focus on post-breach detection and response technologies over pre-breach prevention technologies. Within detection, we are currently excited about the network and infrastructure security bucket and recently invested in MistNet, a threat detection platform that leverages technology based on mist-computing to push AI-based threat detection to the edge.
- Invest behind companies that enable security of the new software infrastructure. This includes cloud and data security companies that cater to a hybrid cloud world and application security companies that secure agile development workflows. We have already invested in two companies that secure hybrid cloud environments – Fortanix, which enables runtime encryption, and CloudKnox, which provides least privilege access management – and are actively looking at a number of other companies.
- Protect IT, OT and supply chain security within the hardware attack vector. We believe that the existing players in these buckets are ripe for disruption and that, in the next 5-7 years, we will see the potential for multiple billion-dollar IPO-worthy companies that protect enterprises from such types of attack.
- Reduce human vulnerability by investing behind messaging security and cyber awareness training. We believe that future technologies will combine email security, phishing simulation, and cyber awareness training. These technologies will develop personalized defenses for employees by alerting them to cybersecurity vulnerabilities that they pose to their enterprise and by helping them to correct their risky behavior.
- Focus on software that uses advances in AI to reduce false positives (vs. creating new alerts) and automates existing processes. We are looking closely at both the security operations/incident response and MSSP buckets within the sector landscape to scope out startups that help security organizations augment their current team while also reducing lower tier alerts and improving the long hours that professionals in the industry currently face. This was also the reason for our investment in Respond Software, which has created a new process that it calls Robotic Decision Automation to automate security monitoring and triage.
The cybersecurity market is only in its early innings. Before Facebook and LinkedIn were founded in the early 2000s, nobody was comfortable sharing their personal information over the internet. Now it’s estimated that there are over 2.5 billion people using social media platforms to share their information online (over 30% of the global population and over 60% of the global internet population). The same is true for transactions online, with global ecommerce sales now over $3 trillion.
We are big believers in the opportunity ahead for cybersecurity startups. To put things into perspective, the global defense budget for physical armies in 2017 was $1.7 trillion. As we spend more time in the virtual world, isn’t it possible that the total cyber budget will also be over $1 trillion?
Think our thesis resonates with you? Don’t agree with what we said? If you are venturing into the cybersecurity world, then we want to hear from you. We like to partner early and aren’t afraid to take risks to help scale the next generation of cybersecurity leaders.